In the current Tangle a transaction is accountable for its cone of past transactions, i.e. all the transactions that it approves directly or indirectly. This means, for a transaction to be considered valid, we expect that after all the transactions in its past cone have been applied to the Genesis, we get a valid state, in which no balances are negative.
In this topic, we’ll describe an attack vector as a direct consequence of this definition.
Attack Vector
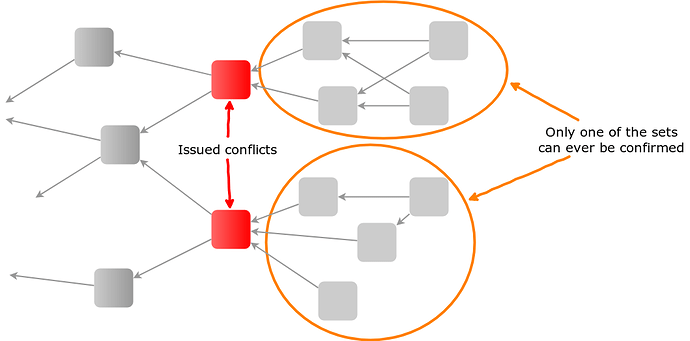
For any consensus mechanism on the Tangle in which conflicts are undecided for a certain amount of time, there is the following attack vector called conflict spamming:
An attacker issues two (or more) conflicting, but individually valid, transactions at the same time. These transactions will be picked up by honest users of the network performing tip selection, leading to a situation in which each of these conflicts will have multiple transactions approving it. This introduces a Tangle split, since no valid transaction can ever approve more than one of these conflicts. Thus, eventually, every transaction approving any but one conflict will become invalid and require re-attaching.
How many transactions will eventually be attached to those conflicts depends on multiple factors like the used tip selection algorithm or the time difference between the issued conflicts, but, in general, each conflict will have a lot of such transactions. This makes conflict spamming dangerous even in situations where an individual attacker is not able to issue many transactions, as even two conflicts alone can potentially “invalidate” hundreds of honest transactions.
Currently, the Coordinator is vulnerable to this attack.